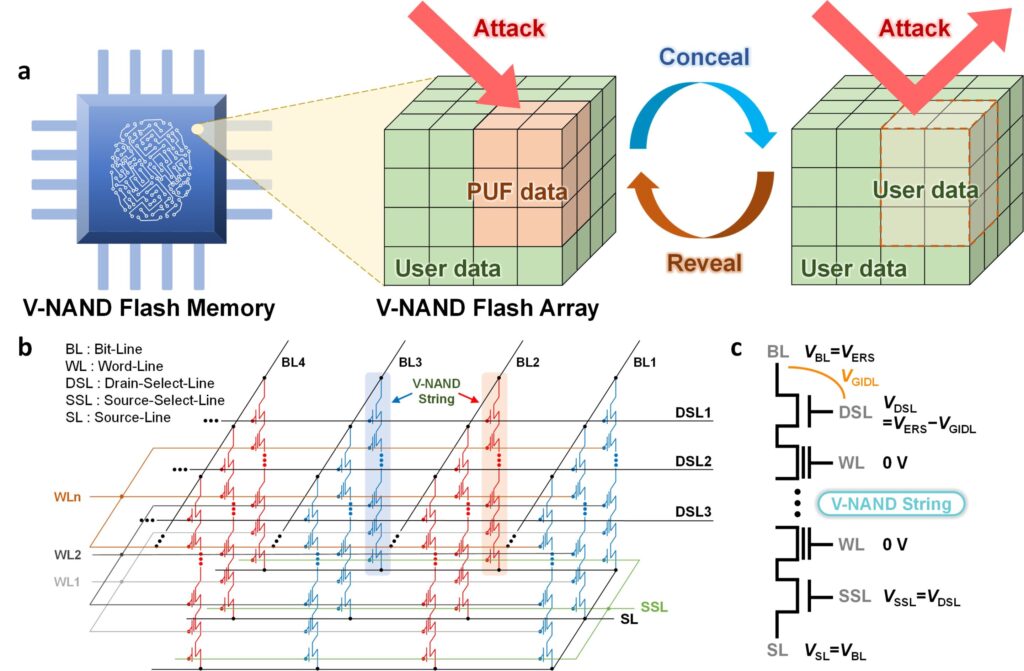
Concealable PUF using GIDL erase in V-Nand flash memory. (a) Schematic diagram of a hidden PUF using V-Nand flash memory. (b) Circuit diagram of a V-Nand flash memory. (c) Explanation of GIDL Elimination Method. Credit: Natural Communication
The Faculty of Engineering, Seoul National University, has announced that the research team has developed new hardware security technology based on commercially available 3D NAND flash memory (V-NAND flash memory).
Named “Hiddenable Physical Infinite Functions (Hiddenable PUFs), this technology maintains the central advantages of traditional PUFs (clenobilization and randomness) while adding new features. This illustrates the world’s first implementation of such a feature on V-Nand flash memory.
The study was published online on June 3rd at Nature Communications. This study was by a research team of Professor John He Lee, of the Faculty of Electrical and Computer Engineering.
The rapid advances in AI and big data have resulted in data usage surged, making data security even more important than ever. Traditional password systems have proven inadequate, and PUF technology has emerged as a promising option. PUFs take advantage of small, naturally occurring physical differences in semiconductor manufacturing to generate cloned or unpredictable unique values. However, traditional PUFs are largely limited to lab-scale devices facing the challenges of mass production and safe concealment.
To overcome these limitations, the researchers adopted a weak application of the GIDL (gate-induced drain leakage) erasing mechanism of v-nand flash memory, intentionally amplifying the variation in erasing levels between memory cells, thereby enabling the generation of PUF data.
Importantly, this approach does not require any circuit or structure changes. This allows PUFs to be implemented directly into widely used V-Nand flash memory. The main advantage of this method is that you can hide your security key under your user data if you are not using it, and can only be revealed when necessary. This optimizes both security and memory space efficiency. The same memory space used to store security keys can be reused for common data storage, allowing for more efficient system design.

PUF key generation and operation method using GIDL erasing on V-Nand flash memory. (a) Vth distribution of V-Nand flash cells after weak erase of GIDL. (b) Comparison of traditional NAND flash-based PUFs with the proposed method. Credit: Natural Communication
The researchers validated the approach using commercial V-Nand flash memory. The generated PUF data maintained 100% accuracy and randomness under a variety of conditions, including over 10 million read cycles from 25°C to 85°C.
The main concealment and iteration functions were repeated over 100 times without error, indicating the reliability of the technique. Furthermore, simulated machine learning attacks were able to predict keys at levels consistent with random inferences, confirming high security of hidden PUFs.
By enabling secure generation, storage, and key concealment in commercial memory components, this sophisticated system has the potential to be powerful for deployment in smartphones, vehicles, and IoT devices that require robust security. The research team plans to expand the application of concealable PUF technology to a wider range of hardware security solutions.
Professor Lee said, “The hidden PUF stands out for its creativity and practicality as it utilizes mass-produced vertical NAND flash memory technology without modification. It is expected to be widely adopted in the field of information security.”
Lead author Sung-Ho Park added: “This study is important as it demonstrates how to implement PUFs using the erase operations of existing V-Nand flash memory without modifying the circuit or design.
Park is currently pursuing an integrated master’s and doctoral program in the Faculty of Electrical and Computer Engineering at Seoul National University. His research interests include improving the properties of V-NAND flash memory, neural computing, and data security.
Details: Sung-Ho Park et al, vertical NAND flash memory, hidden physical disable feature using Nature Communications (2025). doi:10.1038/s41467-025-60415-y
Provided by Seoul National University
Quote: Hardware Security Technology can hide and display encryption keys at demand using 3D flash memory (2025, June 30th). Retrieved July 1, 2025 from https://techxplore.com/news/2025-06-hardware-tech-reveal-encryption-keys.html
This document is subject to copyright. Apart from fair transactions for private research or research purposes, there is no part that is reproduced without written permission. Content is provided with information only.